On the road of smart cars, between the precise arms of industrial robots, or in the sky where UAVs fly smoothly, there is an invisible communication network working silently, which is the CAN (Controller Area Network) bus system.
As the communication backbone in the embedded field, CAN bus undertakes the mission of key data transmission, but the electromagnetic interference, hardware failure and other factors in the transmission process may cause cracks in the perfect data flow.
If the brake command is tampered with a bit in the transmission, or the engine parameters lose part of the information in the transmission, the consequences will be unimaginable.
For this reason, data integrity protection has become the core issue in the design of CAN communication.
Among many error detection mechanisms, checksum has become the first choice for many lightweight applications because of its simplicity and efficiency.
It is like a careful gatekeeper, who does not pursue complex tricks, but can pass the first pass for data packets through simple arithmetic operations. Whether it is the state exchange between automotive electronic control units or the data acquisition of industrial sensors, checksum has won the favor of engineers because of its low cost and easy implementation.
Let’s delve into the secrets of checksum in CAN communication — from its basic principles to actual calculations — to see how this seemingly simple technology guards our digital world.
Checksum is a data check code to check the integrity of communication data.
It is a simple check mechanism, which accumulates all bytes or bits in a data block to obtain a sum, and then performs certain processing (such as modulus) on the sum to generate a check value. It is often used to detect simple errors during data transmission.
Advantage
- It is simple to implement, fast to compute, and suitable for lightweight scenarios.
- Capable of detecting occasional errors such as a single bit flip.
Shortcoming
- Weak detection capability to detect certain complex error patterns such as bit flip order changes or multi-bit errors.
- Some specific errors (such as value exchange, bit exchange, etc.) cannot be detected.
1.check sum checksum
The checksum signal can be used in place of the PV protection values to check for the failure of the controller to send incorrect data.
The checksum value must be in the same frame message as the signal it protects. A single checksum value protects all signals within a frame. In fact, all bits in a frame are protected, whether or not they are part of a particular signal. This is because the checksum is generated based on the entire frame message and not on a single signal.
2.Calculation of checksum
Check sum checksums are usually added directly at the end of the transmitted data. Similarly, it also has a variety of algorithm implementations, such as the cumulative sum check algorithm, the exclusive or check algorithm, and the direct cumulative sum algorithm.
For example, a simple algorithm can divide the data into bytes, each byte into an 8-bit value, and then add the values of all bytes to get the result of Checksum.
- Core role and design purpose
The core purpose of Checksum is to supplement the deficiency of the link layer CRC check of the CAN protocol. The built-in CRC field of CAN bus can effectively ensure the correctness of bit stream in the physical transmission process of data from “one CAN transceiver to another CAN transceiver”.
However, the broadcast mechanism of CAN enables any node to send messages, and the CRC inherent in the protocol cannot verify whether the data source is “legitimate”, nor can it detect errors that have occurred when the data is packaged at the application layer of the sending node or before it is unpackaged at the application layer of the receiving node.
Therefore, Checksum was introduced as an application-layer check to achieve three main goals:
- Ensure that data is packed and unpacked correctly:prevent data errors from occurring during the process of sending node CPU memory to CAN controller, or receiving node CAN controller to CPU memory.
- Implement data encryption and identity authentication:the sender and the receiver agree on a private Checksum algorithm, which is equivalent to a “key”. Illegal nodes who do not know the algorithm are difficult to forge the correct check value, so they can not pretend to be legitimate nodes to communicate, which improves the network security.
- Improve the reliability of the data:through the additional check layer, the probability of undetected data anomalies caused by multi-bit errors is greatly reduced, for example, the error rate of CRC-8 check can be as low as 1/256.
- Location, format and calculation object
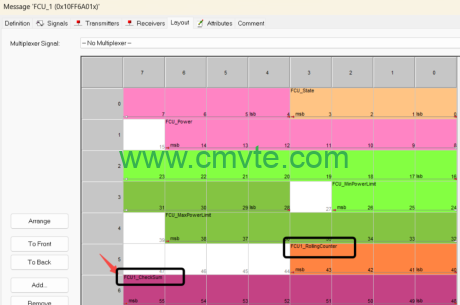
- Location:The Checksum signal is located in the Data Field of the CAN message and usually occupies a complete byte (8 bits), usually the first or last byte of the Data Field.
- Format:It is an independent signal, defined in the DBC (database) file, alongside common signals such as temperature, speed, etc.
- Calculation object:Checksum is calculated for other signals in the data segment of this message (sometimes including the message ID). This is in sharp contrast to the CRC of the can link layer: the calculation objects of the CRC of the link layer include all bits of the frame start, arbitration segment, control segment and data segment, and the check results are stored in an independent CRC segment, which is a fixed component of the can frame format.
- Common algorithms and implementation
The Checksum algorithm is highly flexible and can be defined by the OEMs or suppliers. Common algorithms include:
- Accumulation and negation:Accumulate all the bytes in the data segment (or every two bytes as a group), and perform bitwise negation or Xor of the accumulated sum with a specific value to obtain the final check value.
- CRC algorithm:This is the most common and robust method, and is usually used to calculate data segments with algorithms such as CRC-8, CRC-16, or CRC-32.
In engineering implementation, in order to save computing resources, the look-up table method is often used, that is, the output corresponding to all possible inputs is calculated in advance and made into a table, and the results are obtained directly by looking up the table at runtime, which is very efficient.
- Nibble summation: The message ID and data are unsigned accumulated in units of every 4 bits (one nibble). After overflow processing, the 4-bit check value is obtained by subtracting the accumulated sum from a specific value, which is stored in the lower 4 bits of the last byte of the data segment.
- Synergy with Rolling Counter
In the CAN communication matrix, Checksum is almost always paired with the Rolling Counter signal, which together form the basic “golden partner” for data protection.
- Rolling Counter:a 4-bit counter that is cyclically incremented from 0 to 15, and its value is increased by 1 every time a frame message is sent. It is used to monitor whether the message is lost or out of order.
- Synergy:
- Checksum guarantees the integrity of the data content (the data has not been altered).
- Rolling Counter guarantees the continuity of the data sequence (no frame loss).
- The combination of the two makes it difficult for an attacker to simulate a continuous and correct counter sequence even if he can crack the Checksum algorithm and forge a frame of data, which greatly increases the difficulty of the attack.
- The receiving end can make a judgment by combining the two. For example, if the same Counter value is received for five consecutive times or the Counter jump is greater than 2 for three consecutive times, it is judged as a Counter error.
7.Example of checksum calculation
For example, the checksum signal is defined as 11 bits at the end of a frame. The last byte of the message is the 8 least significant bits of the checksum, and the lower 3 bits of the previous byte are the 3 most significant bits of the checksum.
The value of the checksum is equal to the sum of the first 6 bytes of the message, plus the 5 bits in the same byte as the MSB part of the checksum, plus the CAN ID divided by 8. The calculation formula is:
Dividing by 8 should equal the logical shift right by 3, that is, the sign > > 3 in the formula.
If CAN _ ID is not a multiple of 8, the decimal part should be rounded off.
Assume there is a message ID, $1 FC (decimal 508, binary 00010001)
Byte [0] = $11 = 17 (dec) = 00100010 (bin)
Byte [1] = $44 = 68 (dec) = 01000100 (bin)
Byte [2] = $88 = 136 (dec) = 10001000 (bin)
Byte [3] = $AA = 170 (dec) = 10101010 (bin)
Byte [4] = $BB = 187 (dec) = 10111011 (bin)
Byte [5] = $FF = 255 (dec) = 11111111 (bin)
Byte [6] = 01000xxx (bin) (where “XXX” for 3 bits is part of checksum)
Then,
Checksum =(Byte [0]+ Byte [1] + Byte [2] + Byte [3] + Byte [4] + Byte [5] + ((Byte [6] & 0xF8) >> 3) + (CAN_ID / 8))
= 17 + 68 + 136 + 170 + 187 + 255 + ((01000xxx & 0xF8) >> 3) + (508 / 8)
= 833 + ((01000xxx & 11111000) >> 3) + 63
= 833 + 01000000 >> 3 + 63
= 833 + 00001000 + 63
= 833 + 8 + 63 = 904 (dec)
= $388 (hex)
= 011 10001000 (bin)
Therefore, the complete message with checksum is,
Byte [0] = $11 = 17 (dec) = 00100010 (bin)
Byte [1] = $44 = 68 (dec) = 01000100 (bin)
Byte [2] = $88 = 136 (dec) = 10001000 (bin)
Byte [3] = $AA = 170 (dec) = 10101010 (bin)
Byte [4] = $BB = 187 (dec) = 10111011 (bin)
Byte [5] = $FF = 255 (dec) = 11111111 (bin)
Byte [6] = $43 = 67 (dec) = 01000011 (bin)
Byte [7] = $88 = 136 (dec) = 10001000 (bin)
Through the above detailed introduction and example calculation, we can see that checksum plays a simple but indispensable role in CAN communication. It is like a loyal sentry, guarding the integrity of data in the most direct way, especially suitable for those embedded scenarios with high real-time requirements and limited resources.
However, just as any technology has its boundaries, the limitations of checksum are a reminder that in safety-critical systems, such as autopilot or avionics, it may be necessary to incorporate more powerful checking mechanisms, such as CRC (Cyclic Redundancy Check) or hash functions, to deal with more complex error patterns.
For engineers and developers, mastering checksum is not only the first step in learning the basics of communication, but also an opportunity to develop systems thinking.
In practical projects, a reasonable choice of calibration method requires a trade-off between computational overhead, error detection capability, and system requirements.
For example, in an automotive CAN network, checksum is often used in conjunction with a rolling counter to enhance resistance to replay attacks.
In the future, with the popularity of the Internet of Things and the Internet of Vehicles, data integrity technology will continue to evolve, but the core idea of checksum-solving basic problems with simple logic-will continue to shine.